Начиная с Ubuntu 20.10 при обновлении системы или добавлении репозиториев с помощью apt-add-repository и ключей с помощью apt-key вы можете видеть ошибку Key is stored in legacy trusted.gpg keyring или apt-key is deprecated. Вообще говоря, это не ошибка, а всего лишь предупреждение и всё будет работать не смотря на неё.
Но если вы не хотите видеть это сообщение, можно всё поправить. В этой статье мы рассмотрим как исправить ошибку key is stored in legacy trusted.gpg keyring и почему она возникает.
Содержание статьи
Почему возникает ошибка
Эта ошибка означает, что ключ стороннего репозитория хранится в устаревшем хранилище ключей /etc/apt/trusted.gpg. Это похоже на то, что было несколько лет назад со строками настройки сторонних репозиториев. Сразу они хранились в /etc/apt/sources.list, а потом их перенесли в /etc/apt/sources.list.d/. Но дело не только в этом.
Все пакеты в сторонних репозиториях, которые вы можете добавить в Ubuntu, в том числе и из PPA, должны быть подписаны GPG ключом, который находится в списке доверенных ключей системы. При добавлении репозитория, добавляется не только запись о репозитории в файл /etc/sources.list или /etc/sources.list.d, но и его ключ, который сохранялся в по умолчанию в /etc/apt/trusted.gpg.
Это работает, но проблема в том, что apt полностью доверяет ключам из этого расположения, так же как и из расположения /etc/apt/trusted.gpg.d/. Все эти ключи могут использоваться для проверки подписи всех репозиториев. Например, ключ от Elasticsearch может использоваться для верификации пакетов из репозитория MySQL. Разработчики считают это проблемой безопасности поскольку это может привести к тому, что пакеты из официальных репозиториев могут быть заменены вредоносными из сторонних репозиториев. Они хотят отказаться от кросс-подписи и добиться того, чтобы пакеты из каждого стороннего репозитория проверялись его ключом. При правильной настройке приоритетов это может защитить пакеты из официальных репозиториев от подмены.
Это правильный подход. Но, похоже, на момент написания статьи в Ubuntu 22.04 и Debian 11 подобная защита по умолчанию не реализована. И даже если вы разместите ключи как рекомендуется, пакеты из официальных репозиториев всё ещё могут быть подменены. Таким образом, это задел на будущее. Если я не прав и вы знаете как реализовать такую защиту - расскажите в комментариях.
Для того чтобы воплотить эту идею в жизнь сначала нужно чтобы у каждого репозитория был указан ключ, которым будут проверяться его пакеты. Для этого разработчики рекомендуют сохранять ключи для каждого пакета в отдельных файлах. Не в /etc/apt/trusted.gpg.d/, а /etc/apt/keyrings и указывать в описании репозитория путь к ключу, которым должна быть проверена подпись с помощью опции signed-by.
На данный момент объявлена устаревшей утилита apt-key, а также хранение ключей сторонних репозиториев в общем файле /etc/apt/trusted.gpg. В то же время хранить ключи в /etc/apt/trusted.gpg.d всё ещё можно. И многие репозитории так и делают. Хотя некоторые, тот же Elasticsearch, уже используют новый подход. Этот ход не многое меняет, но это первый шаг, к тому чтобы всё было сделано правильно в будущем.
Как исправить Key is stored in legacy trusted.gpg keyring
Вы могли заметить, что раньше во многих инструкциях рекомендовалось использовать apt-key для добавления ключа, а теперь используется утилита gpg. Фактически, для управления ключами и раньше использовалась утилита gpg, а apt-key выступала в роли оболочки и автоматически указывала нужные параметры. Теперь же нужно всё делать явно. Поэтому для системы ничего не поменялось и новые команды gpg можно использовать в старых версиях дистрибутивов.
Для того чтобы убрать это предупреждение, избежать его появления в будущем и сделать всё правильно, вам надо выполнить несколько шагов:
- Забыть про apt-key и добавлять ключи вручную с помощью gpg;
- Забыть про apt-add-repository и добавлять PPA вручную;
- Перенести все ключи из /etc/apt/trusted.gpg/ в /etc/apt/keyrings и прописать путь к ключу для каждого репозитория.
Предлагаю начать с последнего пункта и перенести все сторонние ключи из файла trusted.gpg в папку /etc/apt/keyrings.
Перенос ключей в /etc/apt/keyrings (правильный способ)
Для того чтобы система не выдавала предупреждение о том, что способ хранения ключей устарел или в будущем улучшить безопасность, нужно переместить все ключи сторонних репозиториев из trusted.gpg в папку /etc/apt/keyrings и прописать путь к ключам для каждого репозитория в /etc/apt/sources.list.d. Сначала надо найти все ключи, которые надо перемещать. Для этого выполните команду:
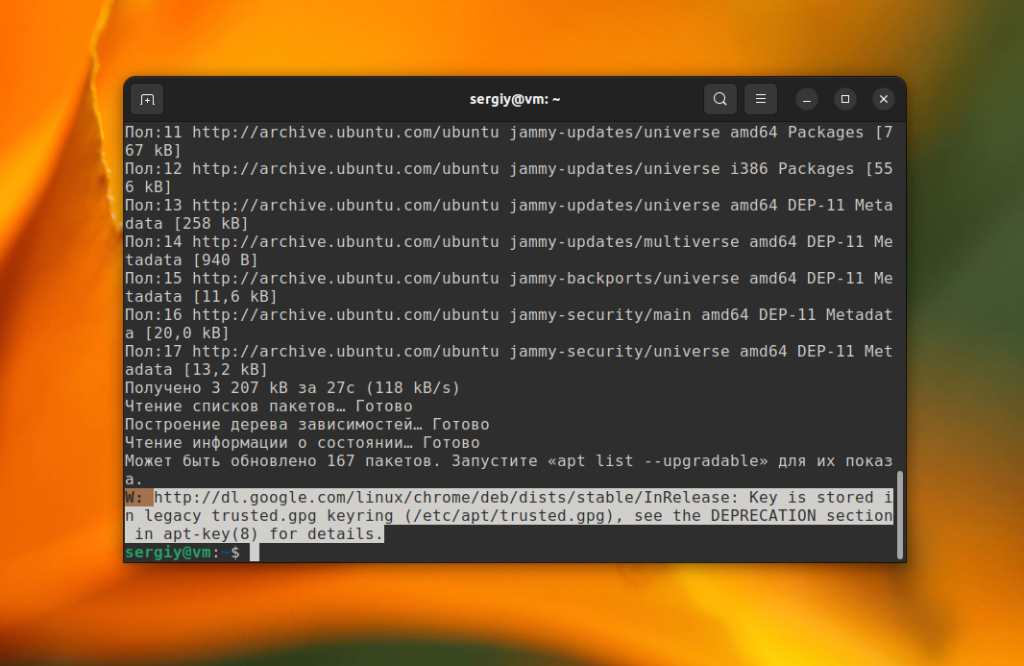
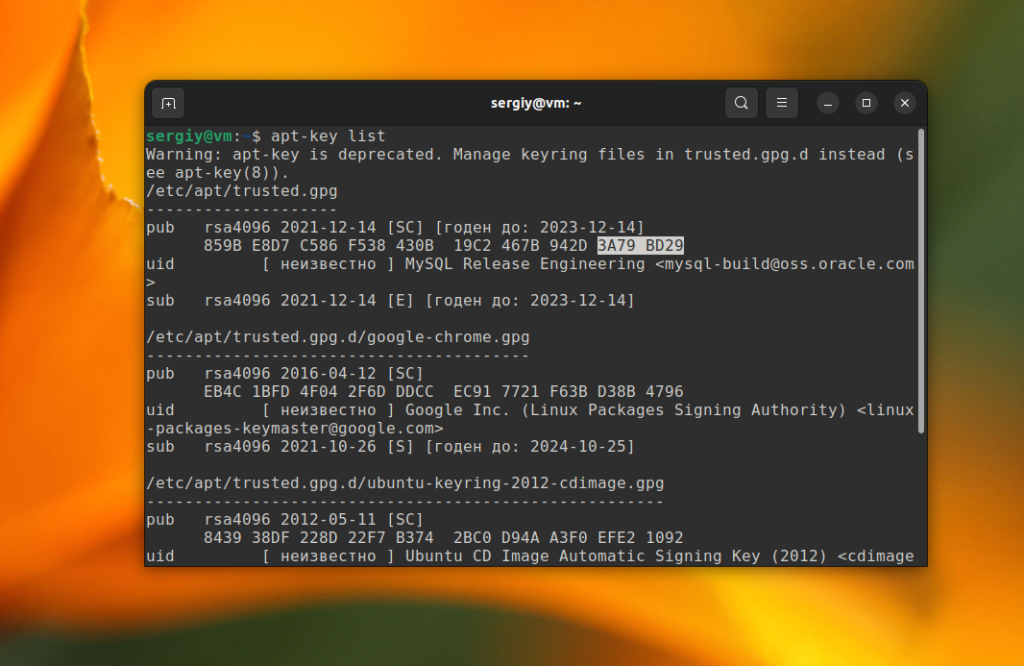
sudo apt-key list
Тут будут выведены все доверенные ключи в системе. Нужно их просмотреть и найти только те, которые хранятся в trusted.gpg. Обычно в выводе утилиты все ключи разделены по файлам и ключи из trusted.gpg будут в самом верху. В данном примере, это ключ от репозитория MySQL. Кроме того, здесь есть ключ от Google Chrome, но он находится в trusted.gpg.d и apt это пока устраивает. Но для улучшения безопасности в будущем вы можете его тоже переместить в /etc/apt/keyrings.
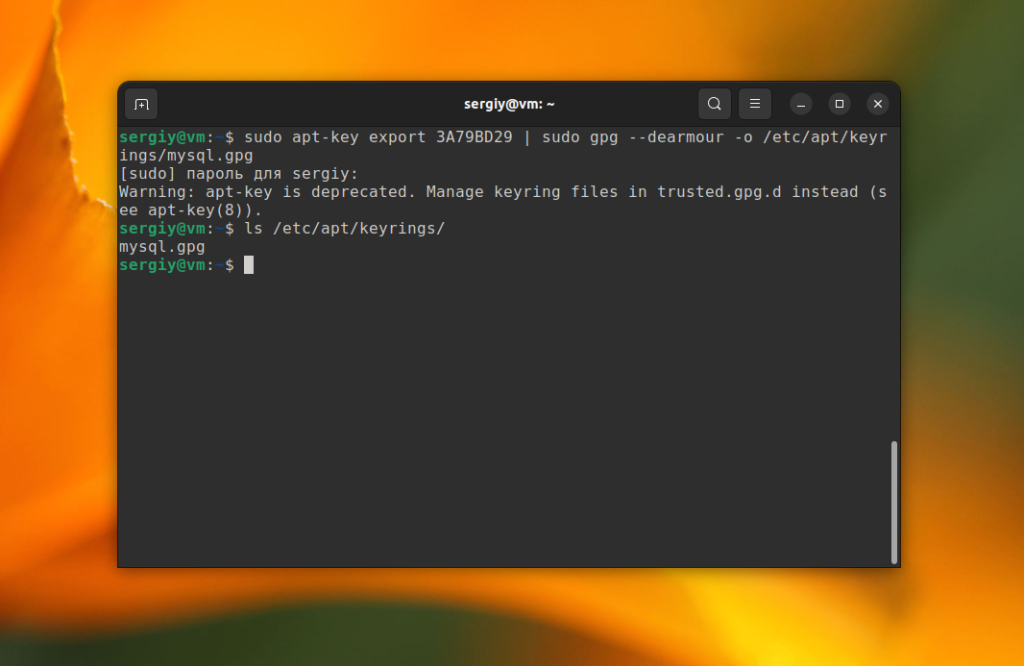
Для того чтобы экспортировать ключ в отдельный файл найдите строчку pub, и возьмите из неё последние 8 цифр. В данном примере это 3A79BD29. Затем выполните такую команду:
sudo apt-key export 3A79BD29 | sudo gpg --dearmour -o /etc/apt/keyrings/mysql.gpg
Имя файла тут не имеет большого значения, однако для того чтобы вы потом понимали к какому репозиторию относится ключ, файлам ключей лучше давать осмысленные имена.
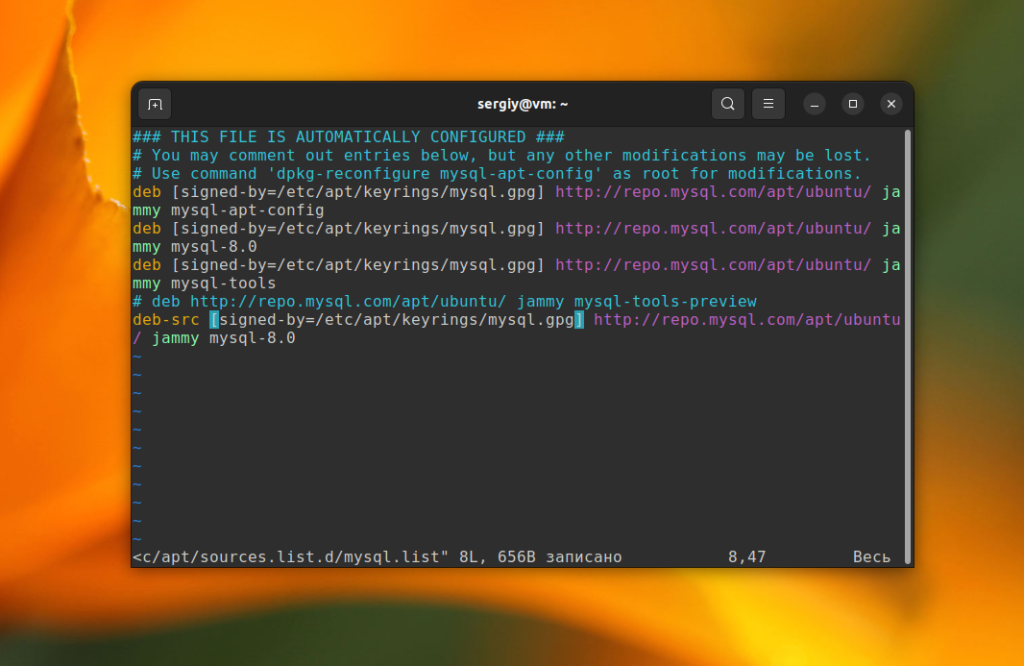
Такую процедуру надо проделать с каждым ключом. Затем для каждого репозитория нужно прописать ключ, которым которым он будет проверяться. В данном примере репозиторий добавлен с помощью файла /etc/apt/sources.list.d/mysql.list. Для каждой строчки deb в этом файле нужно добавить опцию signed-by с путем к ключу. Например:
/etc/apt/sources.list.d/mysql.list
deb [signed-by=/etc/apt/keyrings/mysql.gpg] http://repo.mysql.com/apt/ubuntu/ jammy mysql-apt-config
deb [signed-by=/etc/apt/keyrings/mysql.gpg] http://repo.mysql.com/apt/ubuntu/ jammy mysql-8.0
deb [signed-by=/etc/apt/keyrings/mysql.gpg] http://repo.mysql.com/apt/ubuntu/ jammy mysql-tools
Если там уже есть другие опции, то каждая новая опция должна быть отделена запятой. После этого можно удалить ключ из хранилища trusted.gpg:
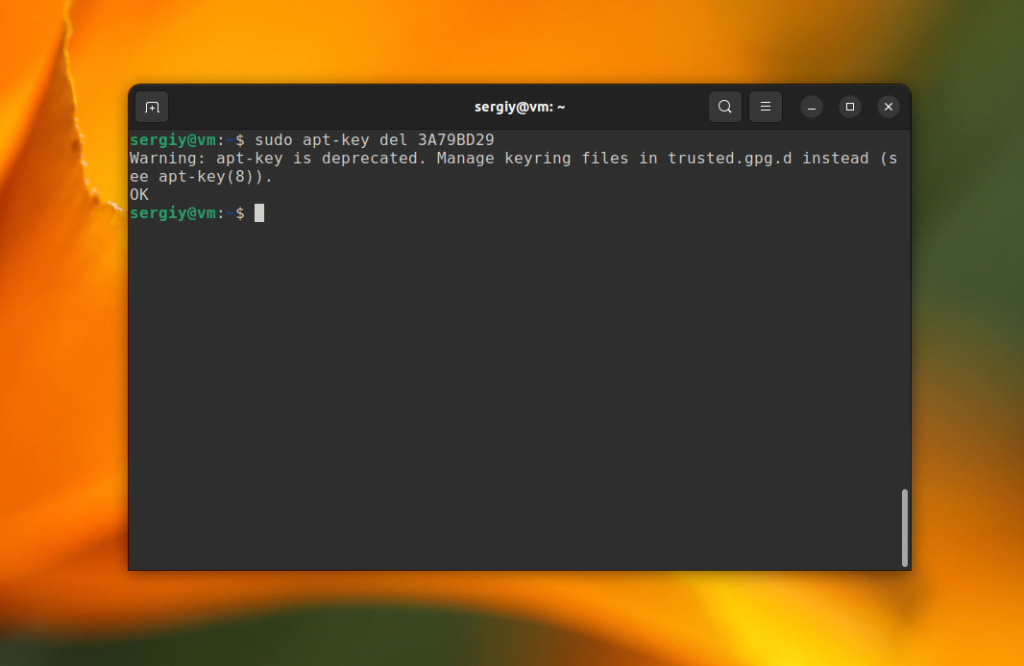
sudo apt-key del 3A79BD29
Дальше вы можете выполнить команду обновления и убедится что больше нет никаких ошибок:
sudo apt update
Перенос ключей в /etc/apt/trusted.gpg.d/ (допустимый способ)
Как я уже говорил выше, на данный момент объявлено устаревшим только хранение ключей в trusted.gpg. Если вы не хотите прописывать signed-by для всех репозиториев, то всё ещё можете переместить ключи в trusted.gpg.d. Тогда они все ещё будут использоваться для проверки подписи пакетов из всех репозиториев, но apt не будет выдавать предупреждение при обновлении. Порядок действий тот же. Сначала надо посмотреть список ключей в trusted.gpg:
sudo apt-key list
Затем экспортировать каждый ключ в trusted.gpg.d. Например:
sudo apt-key export 3A79BD29 | sudo gpg --dearmour -o /etc/apt/trusted.gpg.d/mysql.gpg
И удалить его из trusted.gpg:
sudo apt-key del 3A79BD29
В данном случае, прописывать ключи в signed-by для каждого репозитория не надо, поскольку они и так считаются доверенными для всех репозиториев apt.
Если вы выбрали этот способ, то дальше можно не смотреть. Утилита apt-key в последних версиях Ubuntu 22.04 уже сохраняет ключи сторонних репозиториев в /etc/apt/trusted.gpg.d и для того чтобы убрать ошибку достаточно сконвертировать старые ключи. Если же вы хотите сделать так, как рекомендуют разработчики Ubuntu, смотрите дальше.
Как добавить ключ без apt-key
На данный момент утилита apt-key считается устаревшей и добавлять ключи с помощью неё не рекомендуется. Для этого надо использовать gpg. Обратите внимание, что ключи могут быть двух типов. Либо в формате ASCII с расширением .asc либо в бинарном формате .gpg. Но apt может работать только с ключами в формате OpenPGP и расширением .gpg. Поэтому нельзя просто скопировать полученный ключ в папку /etc/apt/trusted.gpg.d или /etc/apt/keyrings.
Обычно ключи распространяются в формате ASCII, вы можете скачать его, конвертирвать и уже затем добавить в систему с помощью gpg. Например, выполните такую команду для загрузки ключа Google Chrome:
wget https://dl.google.com/linux/linux_signing_key.pub
А затем конвертируйте его в бинарный файл:
cat linux_signing_key.pub | sudo gpg --dearmor -o /etc/apt/trusted.gpg.d/chrome.gpg
То же самое можно сделать одной командой:
wget -q -O - https://dl.google.com/linux/linux_signing_key.pub | sudo gpg --dearmor -o /etc/apt/keyrings/chrome.gpg
Ну и не забудьте добавить опцию singed-by для репозитория. Например, для того же Google Chrome новая команда добавления репозитория будет выглядеть так:
sudo sh -c 'echo "deb [arch=amd64 signed-by=/etc/apt/keyrings/chrome.gpg] http://dl.google.com/linux/chrome/deb/ stable main" > /etc/apt/sources.list.d/google.list'
После этого вы можете проверить что всё заработало и ключ распознается корректно.
Если же ключ распространяется в бинарном формате, вы сразу же можете поместить его в хранилище ключей:
wget -q -O - https://url | sudo tee /etc/apt/trusted.gpg.d/reponame.gpg
Как добавить PPA без apt-add-repository
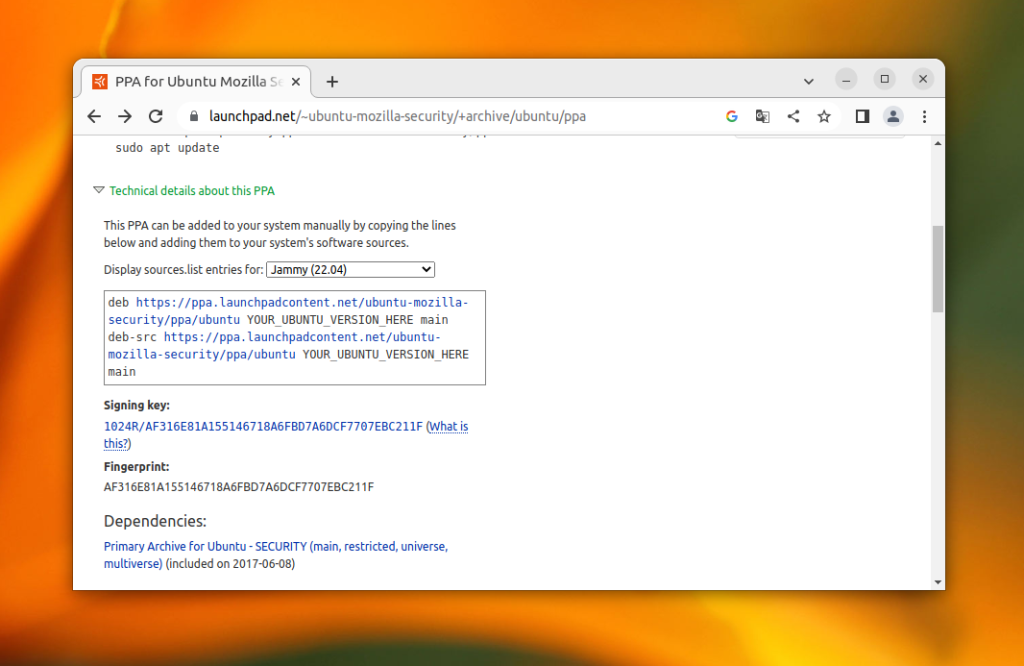
Поскольку apt-add-repository использует apt-key, теперь нельзя использовать эту утилиту для добавления PPA. Простого способа получить путь к репозиторию и его ключ в командной строке по его имени нет, но зато вся необходимая информация есть на странице репозитория. Просто раскройте пункт Technical details about this PPA под командами добавления репозитория. Например, для Firefox:
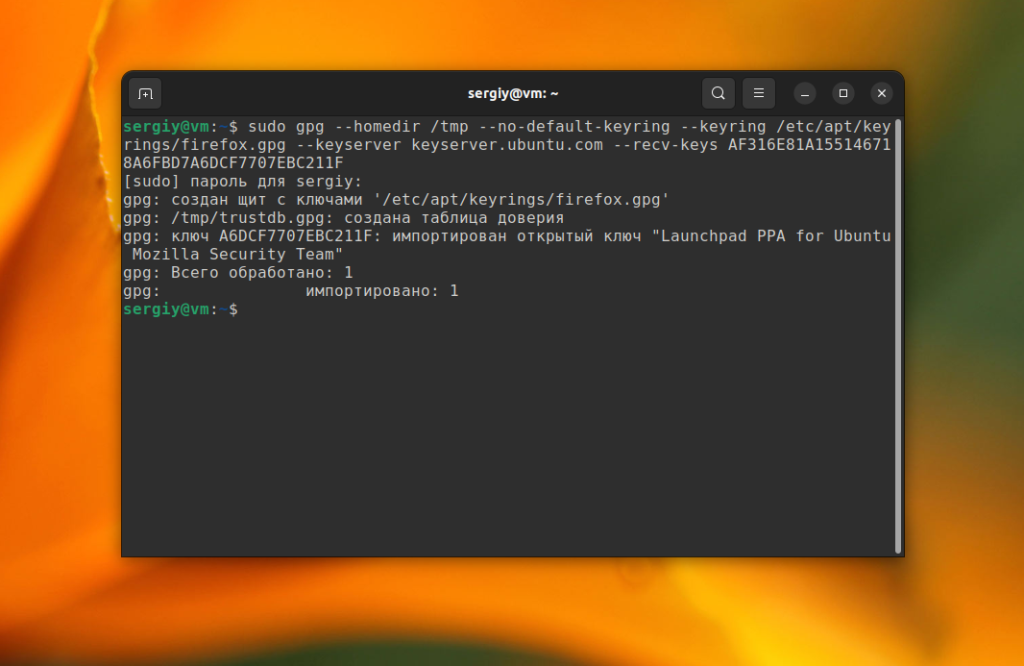
Здесь есть отпечаток ключа, в данном случае AF316E81A155146718A6FBD7A6DCF7707EBC211F. Вы можете добавить ключ в систему с помощью следующей команды:
sudo gpg --homedir /tmp --no-default-keyring --keyring /etc/apt/keyrings/firefox.gpg --keyserver keyserver.ubuntu.com --recv-keys AF316E81A155146718A6FBD7A6DCF7707EBC211F
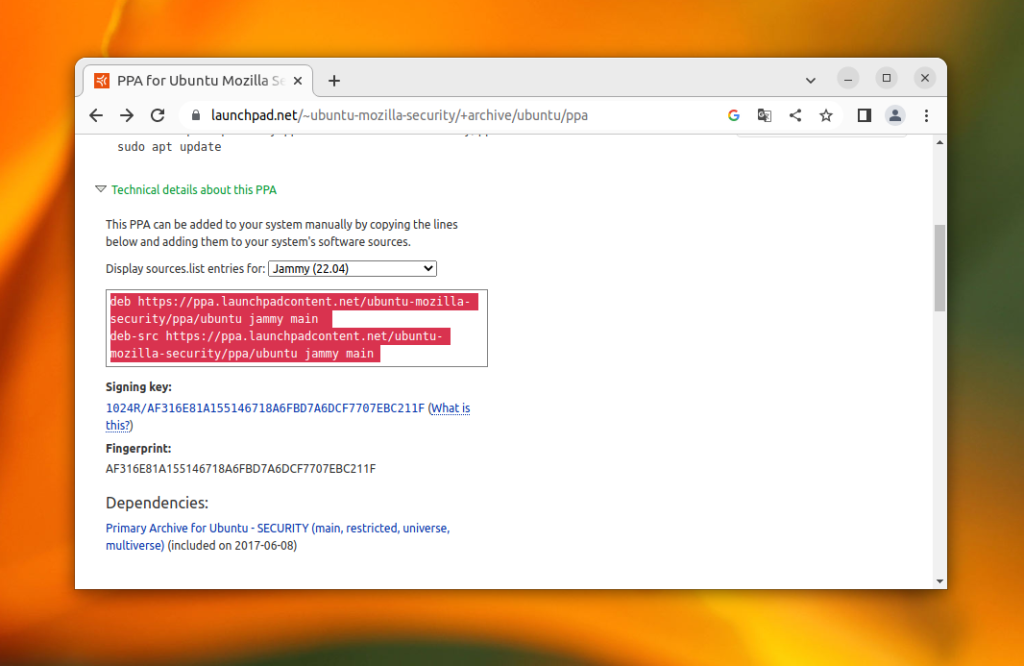
После этого надо добавить запись об этом репозитории в /etc/sources.list.d. На странице PPA выберите версию вашего дистрибутива и скопируйте строки над ключом:
Создайте файл /etc/apt/sources.list.d/firefox.list и вставьте в него то, что было скопировано.
Если вы решили не хранить ключи в /etc/apt/trusted.gpg.d, то вам также нужно прописать путь к ключу репозитория с помощью опции signed-by. Если ключ был сохранен в /etc/apt/keyrings/firefox.gpg, то результат будет выглядеть вот так:
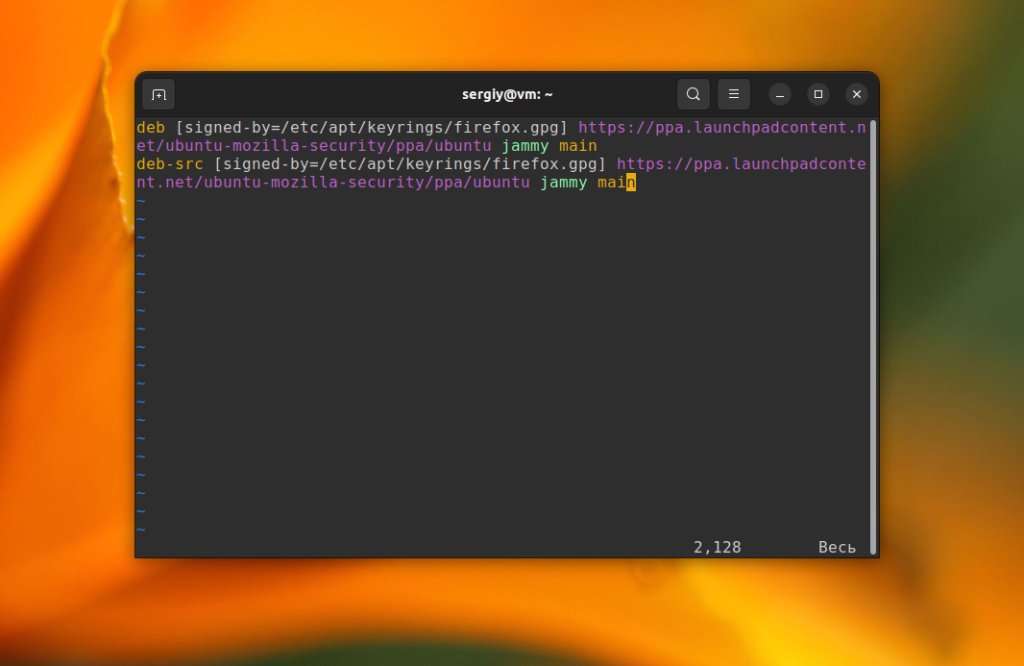
deb [signed-by=/etc/apt/keyrings/firefox.gpg] https://ppa.launchpadcontent.net/ubuntu-mozilla-security/ppa/ubuntu jammy main
deb-src [signed-by=/etc/apt/keyrings/firefox.gpg] https://ppa.launchpadcontent.net/ubuntu-mozilla-security/ppa/ubuntu jammy main
После этого вы можете обновить список пакетов и убедится что всё работает.
Выводы
Теперь вы знаете что означает Key is stored in legacy trusted.gpg keyring и как исправить эту ошибку. Разработчики затеяли серьезное и важное преобразование системы безопасности пакетного менеджера, но это всё ещё довольно сложно для простых пользователей. Намного проще добавить ключ с помощью apt-key и добавить репозиторий по его имени с помощью apt-add-repository. Возможно, в будущем эти утилиты будут обновлены и начнут поддерживать новый способ работы с ключами.
Многие репозитории уже предлагают правильные команды для установки их в систему. А для всех остальных вы можете делать всё вручную, продолжить использовать apt-key или же просто игнорировать предупреждение о том, что ключи хранятся в устаревшем месте.

Anubis – это максимально легкое open-source решение, созданное специально для защиты небольших веб-ресурсов от бесконечного потока запросов от ботов и AI парсеров. Этот инструмент можно считать "ядерным вариантом", потому что он заставляет ботов выполнять вычисления похожие на майнинг криптовалюты. Но это неплохая альтернатива для тех, кто не может или не хочет использовать Cloudflare. Посмотреть детали


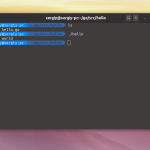
Очень часто:
"W: file:/var/lib/preinstalled-pool/dists/jammy/Release.gpg: Key is stored in legacy trusted.gpg keyring (/etc/apt/trusted.gpg), see the DEPRECATION section in apt-key(8) for details."
Вы можете решить это, набрав в терминале:sudo cp /etc/apt/trusted.gpg /etc/apt/trusted.gpg.d
Ты лучший, дружище!)
Все исправилось ГОРАЗДО проще. Переходим в /etc/atp/ и вижу, что файл с "расширением" gpg не в папке trusted.gpg.d . С помощью терминала меняю название и переносим в папку trusted.gpg.d . Все! Обновляем.
Это больше похоже на костыль, в файле /etc/apt/trusted.gpg может содержаться несколько ключей, и просто копируя этот файл, не есть правильно. Все таки в trusted.gpg.d лучше держать "1 файл = 1 ключ" а не иначе, исключение, если для репозитория используется несколько ключей, например: для deb один, а для deb-src другой
"Если там уже есть другие опции, то каждая новая опция должна быть отделена запятой. "
В Debian 11 и 12 - пробелом
На сколько я знаю - везде так, запятой разделяются несколько значений, например:
deb [arch=amd64,i386 signed-by=/etc/apt/keyrings/mysql.gpg] http://repo.mysql.com/apt/ubuntu/ jammy mysql-apt-config
где у опции arch два значения архитектуры amd64 и i386
А затем конвертируйте его в бинарный файл:
cat linux_signing_key.pub | sudo gpg --dearmor -o /etc/apt/trusted.gpg.d/chrome.gpg
Здесь опечатка, должно быть уже новое место хранения /etc/apt/keyrings/chrome.gpg
Исправил вторым более простым способом. Спасибо.
Считаю что людей которые не делают совместимость вниз ради удовлетворения своих амбиций надо увольнять с работы, а не держать на таких крупных проектах.
sudo apt-key del 3A79BD29 - удалило ключи по обоим путям: старому и новому